- Market services
- Indigenous advisory
-
Compliance audits & reviews
Our audit team undertakes the complete range of audits required of Australian accounting laws to help you to help you meet obligations or fulfil best practice procedures.
-
Audit quality
We are fiercely dedicated to quality, use proven and globally tested audit methodologies, and invest in technology and innovation.
-
Financial reporting advisory
Our financial reporting advisory team helps you understand changes in accounting standards, develop strategies and communicate with your stakeholders.
-
Audit advisory
Grant Thornton’s audit advisory team works alongside our clients, providing a full range of reviews and audits required of your business.

-
Corporate tax & advisory
We provide comprehensive corporate tax and advisory service across the full spectrum of the corporate tax process.
-
Private business tax & advisory
We work with private businesses and their leaders on all their business tax and advisory needs.
-
Tax compliance
We work alongside clients to manage all tax compliance needs and identify potential compliance or tax risk issues.
-
Employment tax
We help clients understand and address their employment tax obligations to ensure compliance and optimal tax positioning for their business and employees.
-
International tax
We understand what it means to manage tax issues across multiple jurisdictions, and create effective strategies to address complex challenges.
-
GST, stamp duty & indirect tax
Our deep technical knowledge and practical experience means we can help you manage and minimise the impact of GST and indirect tax, like stamp duty.
-
Tax law
Our team – which includes tax lawyers – helps you understand and implement regulatory requirements for your business.
-
Innovation Incentives
Our national team has extensive experience navigating all aspects of the government grants and research and development tax incentives.
-
Transfer pricing
Transfer pricing is one of the most challenging tax issues. We help clients with all their transfer pricing requirements.
-
Tax digital consulting
We analyse high-volume and unstructured data from multiple sources from our clients to give them actionable insights for complex business problems.
-
Corporate simplification
We provide corporate simplification and managed wind-down advice to help streamline and further improve your business.
-
Superannuation and SMSF
Increasingly, Australians are seeing the benefits, advantages and flexibility of taking control of their own superannuation and retirement planning.

-
Payroll consulting & Award compliance
Many organisations are grappling with a myriad of employee agreements and obligations, resulting in a wide variety of payments to their people.
-
Cyber resilience
The spectrum of cyber risks and threats is now so significant that simply addressing cybersecurity on its own isn’t enough.
-
Internal audit
We provide independent oversight and review of your organisation's control environments to manage key risks, inform good decision-making and improve performance.
-
Financial crime
Our team helps clients navigate and meet their obligations to mitigate crime as well as develop and implement their risk management strategies.
-
Consumer Data Right
Consumer Data Right (CDR) aims to provide Australians with more control over how their data is used and disclosed.
-
Risk management
We enable our clients to achieve their strategic objectives, fulfil their purpose and live their values supported by effective and appropriate risk management.
-
Controls assurance
In Australia, as with other developed economies, regulatory and market expectations regarding corporate transparency continue to increase.
-
Governance
Through fit for purpose governance we enable our clients to make the appropriate decisions on a timely basis.
-
Regulatory compliance
We enable our clients to navigate and meet their regulatory and compliance obligations.

-
Forensic accounting and dispute advisory
Our team advises at all stages of a litigation dispute, taking an independent view while gathering and reviewing evidence and contributing to expert reports.
-
Investigations
Our licensed forensic investigators with domestic and international experience deliver high quality results in the jurisdictions in which you operate.
-
Digital forensics
Our digital forensic experts identify, preserve and analyse data in the context of reputation and regulatory enforcement issues for investigations, legal or administrative proceedings.
-
eDiscovery
In a data-driven economy, data enables commercial and economic growth, innovation, and social benefit.
-
Asset tracing investigations
Our team of specialist forensic accountants and investigators have extensive experience in tracing assets and the flow of funds.

-
Mergers and acquisitions
Our mergers and acquisitions specialists guide you through the whole process to get the deal done and lay the groundwork for long-term success.
-
Acquisition search & strategy
We help clients identify, finance, perform due diligence and execute acquisitions to maximise the growth opportunities of your business.
-
Selling a business
Our M&A team works with clients to achieve a full or partial sale of their business, to ensure achievement of strategic ambitions and optimal outcomes for stakeholders.
-
Operational deal services
Our operational deal services team helps to ensure the greatest possible outcome and value is gained through post merger integration or post acquisition integration.
-
Transaction advisory
Our transaction advisory services support our clients to make informed investment decisions through robust financial due diligence.
-
Business valuations
We use our expertise and unique and in-depth methodology to undertake business valuations to help clients meet strategic goals.
-
Tax in mergers & acquisition
We provide expert advice for all M&A taxation aspects to ensure you meet all obligations and are optimally positioned.

-
Corporate finance
We provide effective and strategic corporate finance services across all stages of investments and transactions so clients can better manage costs and maximise returns.
-
Debt advisory
We work closely with clients and lenders to provide holistic debt advisory services so you can raise or manage existing debt to meet your strategic goals.
-
Working capital optimisation
Our proven methodology identifies opportunities to improve your processes and optimise working capital, and we work with to implement changes and monitor their effectiveness.
-
Capital markets
Our team has significant experience in capital markets and helps across every phase of the IPO process.
-
Debt and project finance raising
Backed by our experience accessing full range of available funding types, we work with clients to develop and implement capital raising strategies.
-
Private equity
We provide advice in accessing private equity capital.
-
Financial modelling
Our financial modelling advisory team provides strategic, economic, financial and valuation advice for project types and sizes.
-
Payments advisory
We provide merchants-focused payments advice on all aspects of payment processes and technologies.

-
Voluntary administration & DOCA
We help businesses considering or in voluntary administration to achieve best possible outcomes.
-
Corporate insolvency & liquidation
We help clients facing corporate insolvency to undertake the liquidation process to achieve a fair and orderly company wind up.
-
Complex and international insolvency
As corporate finance specialists, Grant Thornton can help you with raising equity, listings, corporate structuring and compliance.
-
Safe Harbour advisory
Our Safe Harbour Advisory helps directors address requirements for Safe Harbour protection and business turnaround.
-
Bankruptcy and personal insolvency
We help clients make informed choices around bankruptcy and personal insolvency to ensure the best personal and stakeholder outcome.
-
Creditor advisory services
Our credit advisory services team works provides clients with credit management assistance and credit advice to recapture otherwise lost value.
-
Small business restructuring process
We provide expert advice and guidance for businesses that may need to enter or are currently in small business restructuring process.
-
Asset tracing investigations
Our team of specialist forensic accountants and investigators have extensive experience in tracing assets and the flow of funds.

-
Independent business reviews
Does your company need a health check? Grant Thornton’s expert team can help you get to the heart of your issues to drive sustainable growth.
-
Commercial performance
We help clients improve commercial performance, profitability and address challenges after internal or external triggers require a major business model shift.
-
Safe Harbour advisory
Our Safe Harbour advisory helps directors address requirements for Safe Harbour protection and business turnaround.
-
Corporate simplification
We provide corporate simplification and managed wind-down advice to help streamline and further improve your business.
-
Director advisory services
We provide strategic director advisory services in times of business distress to help directors navigate issues and protect their company and themselves from liability.
-
Debt advisory
We work closely with clients and lenders to provide holistic debt advisory services so you can raise or manage existing debt to meet your strategic goals.
-
Business planning & strategy
Our clients can access business planning and strategy advice through our value add business strategy sessions.
-
Private business company secretarial services
We provide company secretarial services and expert advice for private businesses on all company secretarial matters.
-
Outsourced accounting services
We act as a third-party partner to international businesses looking to invest in Australia on your day-to-day finance and accounting needs.
-
Superannuation and SMSF
We provide SMSF advisory services across all aspects of superannuation and associated tax laws to help you protect and grow your wealth.
-
Management reporting
We help you build comprehensive management reporting so that you have key insights as your business grows and changes.
-
Financial reporting
We help with all financial reporting needs, including set up, scaling up, spotting issues and improving efficiency.
-
Forecasting & budgeting
We help you build and maintain a business forecasting and budgeting model for ongoing insights about your business.
-
ATO audit support
Our team of experts provide ATO audit support across the whole process to ensure ATO requirements are met.
-
Family business consulting
Our family business consulting team works with family businesses on running their businesses for continued future success.
-
Private business taxation and structuring
We help private business leaders efficiently structure their organisation for optimal operation and tax compliance.
-
Outsourced CFO services
Our outsourced CFO services provide a full suite of CFO, tax and finance services and advice to help clients manage risk, optimise operations and grow.
-
ESG & sustainability reporting
There is a growing demand for organisations to provide transparency on their commitment to sustainability and disclosure of the nonfinancial impacts of their business activities. Commonly, the responsibility for sustainability and ESG reporting is landing with CFOs and finance teams, requiring a reassessment of a range of reporting processes and controls.
-
ESG & sustainability advisory
With the ESG and sustainability landscape continuing to evolve, we are focussed on helping your business to understand what ESG and sustainability represents and the opportunities and challenges it can provide.

-
Management consulting
Our management consulting services team helps you to plan and implement the right strategy to deliver sustainable growth.
-
Financial consulting
We provide financial consulting services to keep your business running so you focus on your clients and reaching strategic goals.

-
China practice
The investment opportunities between Australia and China are well established yet, in recent years, have also diversified.
-
Japan practice
The trading partnership between Japan and Australia is long-standing and increasingly important to both countries’ economies.
-
India practice
It’s an exciting time for Indian and Australian businesses looking to each jurisdiction as part of their growth ambitions.
-
Singapore practice
Our Singapore Practice works alongside Singaporean companies to achieve growth through investment and market expansion into Australia.

-
 Insight Identify your opportunities in the complex landscape of fuel tax creditsThe landscape of fuel tax credits (FTC) is constantly evolving due to ongoing economic and technological developments. This dynamic environment presents both challenges and opportunities for businesses with significant fuel consumption.
Insight Identify your opportunities in the complex landscape of fuel tax creditsThe landscape of fuel tax credits (FTC) is constantly evolving due to ongoing economic and technological developments. This dynamic environment presents both challenges and opportunities for businesses with significant fuel consumption. -
 Client Alert March 2024 Update: NSW Grants for Net Zero Manufacturing and Physical SciencesSome major NSW grant programs have been announced, supporting projects in clean technology innovation, low carbon product manufacturing, renewable manufacturing and physical sciences.
Client Alert March 2024 Update: NSW Grants for Net Zero Manufacturing and Physical SciencesSome major NSW grant programs have been announced, supporting projects in clean technology innovation, low carbon product manufacturing, renewable manufacturing and physical sciences. -
 Insight Navigating a complex Agribusiness, Food and Beverage deals landscape in 2024Despite a 14% global decline in Agribusiness, Food, and Beverage M&A deals, 2024 shows promise with expected global interest rate stabilisation. Given the sector's role in global sustainability, businesses can tap into opportunities in food manufacturing and waste minimisation.
Insight Navigating a complex Agribusiness, Food and Beverage deals landscape in 2024Despite a 14% global decline in Agribusiness, Food, and Beverage M&A deals, 2024 shows promise with expected global interest rate stabilisation. Given the sector's role in global sustainability, businesses can tap into opportunities in food manufacturing and waste minimisation. -
 Client Alert Grants: February 2024Businesses should be aware of the numerous grant opportunities available from Commonwealth, State, and private sources. These grants could be the key to making manufacturing, agriculture, and green economy projects a reality.
Client Alert Grants: February 2024Businesses should be aware of the numerous grant opportunities available from Commonwealth, State, and private sources. These grants could be the key to making manufacturing, agriculture, and green economy projects a reality.
-
Renewable Energy
Transformation through energy transition

-
Business Planning and Strategy
Having an honest, broad-reaching and thought-provoking discussion with a skilled, independent advisor can be the catalyst for clarity – a direction to take your business forward and an understanding of what is key to success.

-
Flexibility & benefits
The compelling client experience we’re passionate about creating at Grant Thornton can only be achieved through our people. We’ll encourage you to influence how, when and where you work, and take control of your time.
-
Your career development
At Grant Thornton, we strive to create a culture of continuous learning and growth. Throughout every stage of your career, you’ll to be encouraged and supported to seize opportunities and reach your full potential.
-
Diversity & inclusion
To be able to reach your remarkable, we understand that you need to feel connected and respected as your authentic self – so we listen and strive for deeper understanding of what belonging means.
-
In the community
We’re passionate about making a difference in our communities. Through our sustainability and community engagement initiatives, we aim to contribute to society by creating lasting benefits that empower others to thrive.
-
Graduate opportunities
As a new graduate, we aim to provide you more than just your ‘traditional’ graduate program; instead we kick start your career as an Associate and support you to turn theory into practice.
-
Vacation program
Our vacation experience program will give you the opportunity to begin your career well before you finish your degree.
-
The application process
Applying is simple! Find out more about each stage of the recruitment process here.
-
FAQs
Got questions about applying? Explore frequently asked questions about our early careers programs.
-
Our services lines
Learn about our services at Grant Thornton
-
Current opportunities
Current opportunities
-
Remarkable people
Our team members share their remarkable career journeys and experiences of working at Grant Thornton.
-
Working at Grant Thornton
Explore our culture, benefits and ways we support you in your career.
-
Current opportunities
Positions available.
-
Contact us
Get in touch

CPS 230 requires regulated entities to consider service disruption from a different perspective. Working backwards through a scenario, entities must identify the harm that a disruption may cause to its customers or the broader financial system, then take active measures to prevent it (operational risk) and recover from it (operational resilience).
Welcome to the third in our series of CPS 230 technical guides.
In the discussion paper that accompanied the issue of draft CPS 230, APRA noted that one of its key objectives is to focus the Board on the importance of operational resilience through requiring the setting of tolerance levels for disruptions to critical operations. Although the approach to set the tolerances should leverage that for setting risk appetite tolerances, the fundamental difference is that when considering operational resilience, the risk is crystallised.
In this guide we set out an approach to assessing operational resilience. The approach leverages the methodology developed by Grant Thornton in the UK where similar requirements have been in place for some time.
Why is operational resilience important?
A robust and resilient financial services sector is essential to preventing financial harm. CPS 230, with its focus on operational resilience, is consistent with prudential requirements in the UK and Europe. It forms part of a suite of APRA requirements related to limiting financial harm due to disruption, including identifying domestic systemically important banks (D-SIBs), CPS 232 Business Continuity Management, CPS 190 Recovery and Exit Planning and multiple capital adequacy and liquidity requirements.
Operational resilience refers to the collective steps an entity takes to minimise the impact and disruption of operational risk incidents. Business continuity and business resilience aim to keep the entity as a whole operating. Operational resilience is related but differs in that the focus is not on the entity as a whole, but the key financial services it delivers.
Although APRA accepts that some degree of service disruption and outages will occur, it is important that regulated entities:
- Have the resilience to get critical operations back up and running without causing financial harm;
- Work within a pre-defined tolerance level that aligns with their broader risk appetite; and
- Conduct robust scenario testing, using extreme but plausible scenarios, to assess whether it is possible to remain within the tolerances set.
The Board is expected to oversee and approve all aspects of operational resilience. As such, risk reporting and Board Risk Committee Charters may need to be updated to include information necessary to facilitate this. Operational resilience will also need to be reflected in risk management declarations.
Identifying critical operations
CPS 230 defines critical operations as processes that:
“If disrupted beyond tolerance levels would have a material adverse impact on its depositors, policyholders, beneficiaries or other customers or its role in the financial system.”
CPS 230 sets out the processes that it expects at a minimum to be identified as critical operations.
At its core, CPS 230 requires regulated entities to prioritise critical services over their own operational objectives to prevent financial harm to consumers. This means, for example, that in the event of a major disruption, APRA expects that priority will be given to restoring core banking operations over other revenue-generating non-regulated businesses.
Resilience planning
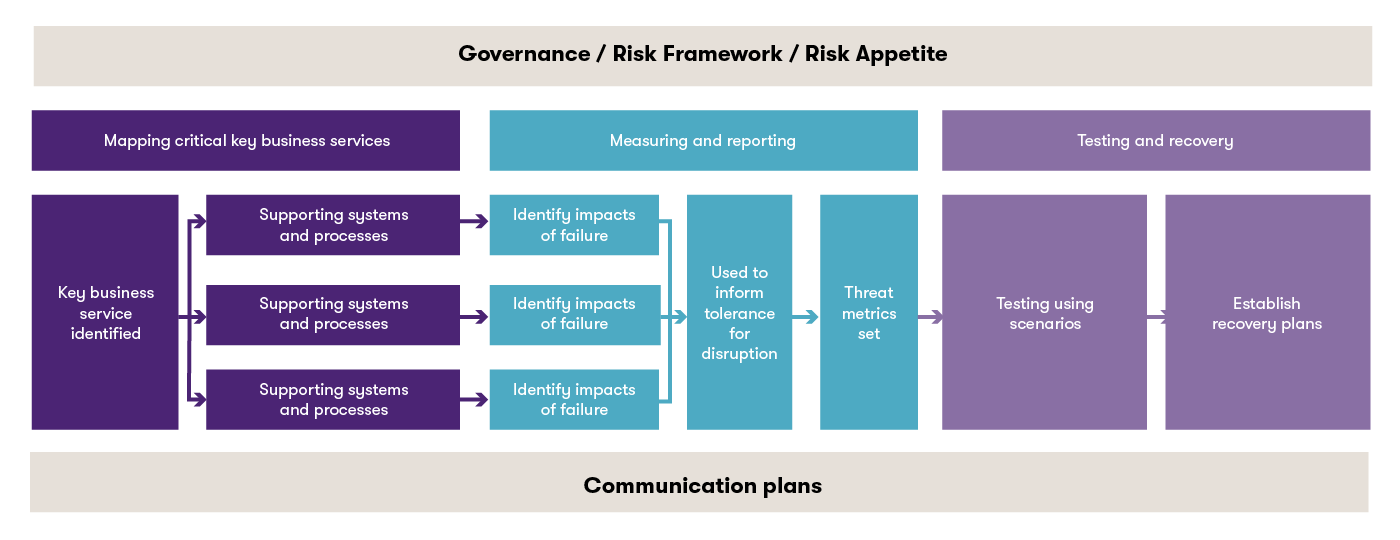
The following diagram sets out the steps necessary for effective resilience planning and key considerations:
The necessary steps can be summarised as:
Activity |
Detail |
Identify |
For each critical process determine how much disruption could be tolerated and under what circumstances. This will require contingency and continuity planning, including identifying back-up or substitute systems, processes and service providers. |
Map |
Document the systems and workflows that support each critical process including activities undertaken by related and non-related service providers. Interdependencies between systems and processes must be identified so that the total impact of any disruption can be assessed. |
Assess |
Determine how the failure of a system, workflow or service provider would impact a critical process. Concentration of critical service providers may increase the impact. Contingency plans must address the disruption and identify potential substitutions. |
Test |
Use severe but plausible scenarios and past experience (for example, COVID) to test that the resilience of each critical process is within tolerance should a disruption occur. Generating scenarios will require involvement from IT, the business, risk and third-party service providers. Testing plans should consider the type and frequency of testing. |
Invest |
Where the resilience is below tolerance, the capacity to respond and recover from disruptions must be enhanced. The focus of enhancements should be to reduce the overall recovery time. |
Communicate |
Identify all internal and external stakeholders, what needs to be communicated, to whom and when. The overall objective of the communications is to enable customers to make informed decisions in the event of an outage. |
The steps will need to be undertaken on a continuous basis to take account of emerging risks, the results of testing and any disruptions that may occur.
CPS 230 sets out the minimum tolerances that the Board must establish for each critical operation:
- Maximum tolerable duration or volume of disruption;
- Maximum extent of data loss; and
- Minimum service levels the entity would maintain while operating under alternative arrangements during a disruption.
Additional metrics that could be established to measure disruption include:
- Number of outages within a set timeframe; and
- Number of customers affected by an outage.
The Financial Conduct Authority (FCA) in the UK published a list of root causes of disruptions to help inform operational resilience planning. These are useful when considering possible scenarios:
- Failure of a change initiative – contributing factors identified were:
- Ill-defined benefits and programme requirements
- Poorly articulated delivered approach
- Lack of acceptance due to poor engagement
- Unrealistic delivery timetables
- Focus on excessive functionality
- Poorly managed changes in project scope
- Ineffective risk management – lack of awareness of dependencies and constraints leading to issues, delays overspend or non-delivery
- Multiple initiatives competing with each other and business as usual for the same resources
- Third party failure
- Change software/application issue
- Cyber attack
- Hardware issue
- Human error
- Process/control failure
- Capacity management
Recovery from disruption will typically include the following steps:
- Emergency response: rapid reaction to a disruption as soon as the issue is discovered
- Crisis management: response and immediate steps taken to remediate the situation
- Business continuity: implementation of existing plans to restore critical operations to an acceptable level within pre-agreed timeframes
- Disaster recovery: restore IT capability and/or physical premises that supports operations
- Restoring business as usual: must include lessons learnt to improve resilience in the long term
- Holistic, joined up approach across all business units and functions
- Understanding of key dependencies across all business units and functions
- Clarity regarding the cost/benefit/risk trade-offs of designing critical processes that is consistent with risk appetite
- Comprehensive, centralised and detailed catalogue of critical processes
- Detailed mapping of processes, services, resources and their criticality